Communications Value-added Business
Overview
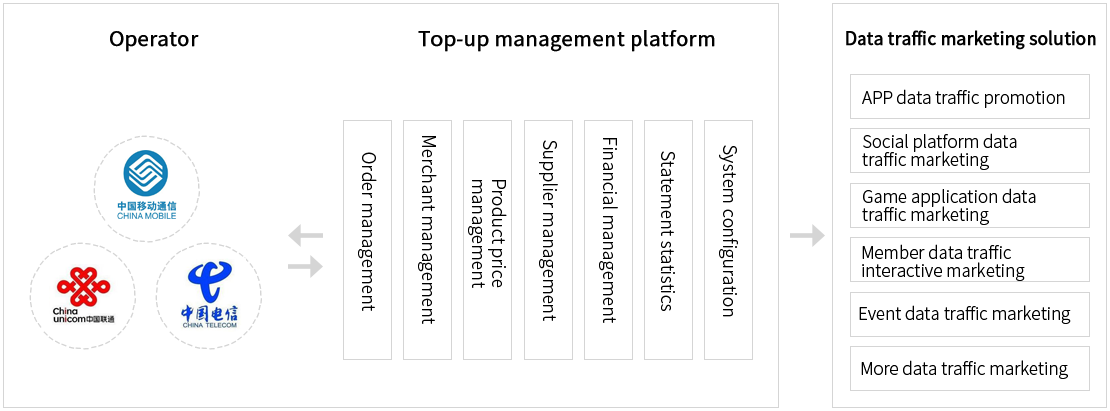
Prepaid recharge and data traffic top-up are supported for users of the three major operators (China Mobile, China Unicom, China Telecom) to help enterprises achieve one-point access, nationwide coverage and seamless integration with business promotion.
Advantages
![]()
Integration of data traffic
of the three operators (China Mobile, China Unicom, China Telecom)
to achieve full coverage of users
![]()
No obstacles nationwide, full coverage of data traffic
![]()
200 user data traffic pushes sent simultaneously,
which is efficient and concurrent
![]()
Accurate and clear order flow, comprehensive grasp of financial revenue and expenditure, real-time reconciliation
![]()
H5 interface, accessibility of SDK and API interfaces
Platform ability
Internet Value-added Services
![]()
Game operation
Business requirements
Advantages
![]()
Video music
Aggregation of service resources

Smart Big Data Value-added Services
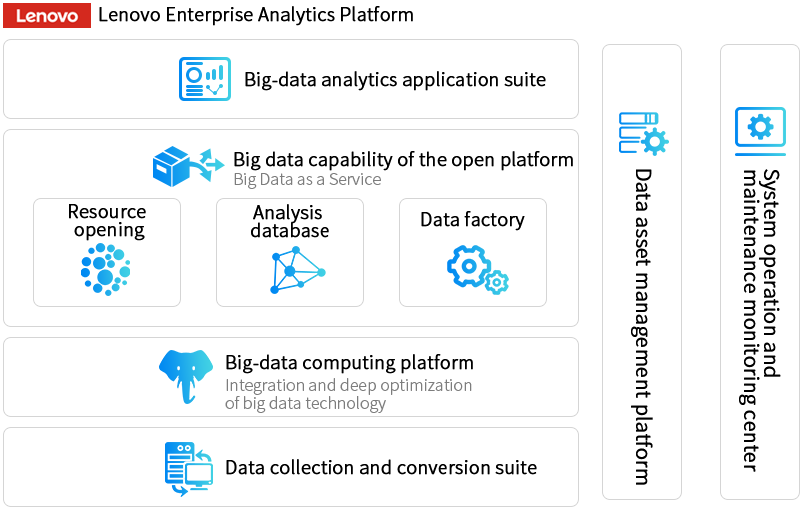
Lenovo Big Data Enterprise Analysis Platform (LEAP)
Ability to manage and control the data lifecycle
Efficient and quick data analysis capability
Deeply optimized data processing capability
All-source heterogeneous data access capability
Enhanced data control capability
Operation and maintance with high efficiency and visualization
Platform Architecture Diagram
Big data building and operation services
End-to-end, helping users dig deeper into data value and enhance business capabilities
![]()
Planning and design
![]()
Platform building
![]()
Data governance
![]()
Value exploration
![]()
Integration custom
![]()
Sustainable operation
![]()
Innovation incubation
Perfect service
Supporting services strongly associated with user business scenarios

Business consulting service
ananced analysis service
IT/OT planning service
Data management service
Mobile terminal device server
Storage
IT/Technical support
Operation and maintance


Tools and application software
Capability of the open platform
Big-data computing platform
Big Data Solutions
Overview
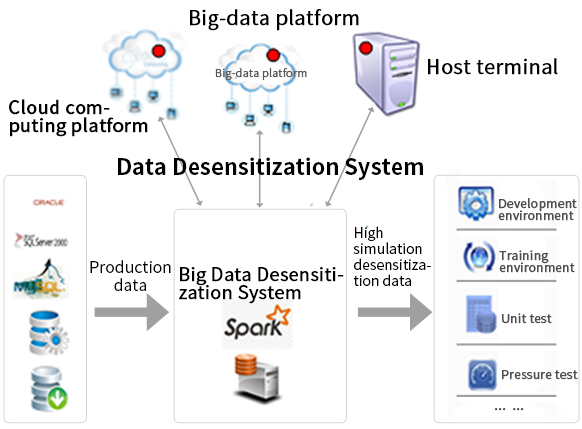
The Big Data Desensitization System is an integrated software-hardware device that uses big-data analysis technology to deliver functions such as privacy data discovery, data extraction, data bleaching, test-data management and data loading. It is characterized by a triumvirate of powerful benefits: process streamlining, automation and job multiplexing.
As a software-hardware integrated device, it is easy to deploy and use, with powerful functionality and out-of-the-box features. Thus, it significantly reduces the workload for your staff and makes the project life cycle more efficient.
System Composition
The Big Data Desensitization System filters user data through access control and performance monitoring. This gives it the ability to filter privacy data according to user-defined desensitization rules so as to avoid the risk of sensitive data leakage while ensuring the integrity and effectiveness of the operator's business data.
Data Processing
The system is a 4U4-node device, which integrates six subsystems: information configuration; desensitization strategy configuration; data extraction; identity authentication and authorization management; big-data desensitization processing; and desensitization auditing.
Overview
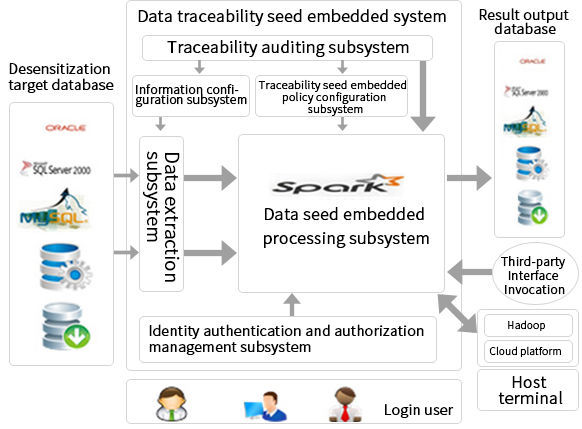
The Big Data Traceability System is a professional device for effective control and traceability of unauthorized diffusion of important corporate data. The system is built on the basis of big-data platform technology, intelligent semantic recognition technology and MMTA matrix hybrid traceability algorithm, making it convenient and fast to use.
System Composition
The data traceability exchange system is composed of two parts. One is the embedded system of traceability seeds, which embeds traceability seeds in data. The other is the traceability analysis function enabled based on the first part.
Traceability Seed Embedded System
The data traceability seed embedded system is composed of six subsystems: information configuration, traceability seed embedded policy configuration, data extraction, identity authentication and authorization management, traceability seed embedded processing, and auditing.

Overview
The system enables distributed and efficient data collection through big data Sqoop technology, as well as quick analysis and inspection of database contents through big-data MapReduce technology. Combined with the inspection of expert database, the system can quickly locate the sensitive information of government affairs and thereby generate detailed inspection and analysis reports on confidential information.
System Composition
The product is an integrated hardware-software device mainly composed of a data-acquisition subsystem, keyword recognition subsystem, and confidential data analysis and visualization subsystem.

Overview
The Big Data Security Monitoring System combines the trusted computing technology with the big data system, so as to deliver solutions to perfectly building a highly secure big data system.
The Big Data Security Monitoring System can effectively guarantee reliability in architecture, operation, resource allocation, data storage and policy management of the big data system.
System Functions
The system has two functions:
1. Trusted data storage, in which trusted measurement is carried out for key system files and important parameters of the big-data platform by the trusted algorithm on a regular basis, thus the health status of big data is visualized;
2. Trusted behavior identification, which gives it the ability to monitor the security status of the big-data platform in real time and give early warning, so as to achieve security management of the big-data platform as required by the data center. The above two functions make it possible to build a highly secure and trusted big data system.

Overview
The SecBoxV1.0 Big Data Safe is a highly reliable data-encryption product. The system adopts a strong domestic encryption algorithm to efficiently encrypt sensitive data in the big data center, so as to achieve data ciphertext storage and ensure data security inside the big data center. Based on the standard Hadhoop platform, the system can interface with other companies' big-data platforms (including Huawei FusionInsight, etc.) through customized development.
System Composition
The big data safe is an integrated software-hardware data-encryption product, which is mainly composed of software modules such as big data encryption and decryption read-write adaptation subsystem, KMS key management subsystem, and data encryption subsystem, as well as hardware server and hardware encryption card.
The product is available in client mode and clientless mode.
Major Products and Services
We strive to achieve the seamless smart connectivity of devices, clients, networks, data and services